Dynamic Acl on Cisco With Ms Nps
As some of you might know, I’m busy setting up a test environment for Port Based Network Access Control. With Cisco switches this is plain simple, cause when 802.1x fails you can switch to MAB. A bit less secure, but better then nothing. When MAB fails you have the option to switch to Web authentication, a so called Captive Portal. This web authentication is also easy to setup, but the last step was a bit tricky. Very short summary, when the switch, switches to web-authentication, it creates an access control list (ACL) to block all the traffic, but still give the user IP connectivity to open a browser and be able to fill in the credentials and post this form. When the credentials are validated by the RADIUS server, it has to say what the new ACL is, cause otherwise the user has very limited access. Most tutorials on the web (the ones I found), explain this very well, but uses a CiscoSecure ACS. In my situation I don’t have an ACS, but I uses the Microsoft Network Policy Server (NPS) as RADIUS instead. This works fine, but it was a bit hard to find how to define the ACL. (as always afterwards it is quite easy :-)) This tutorial, explains very well how to configure the switch for web authentication with an Cisco ACS, I’m not going to try to do this better, so for the switch settings, please follow that tutorial. When the switch is configured, you have to configure NPS. I assume you already added your device, to the device list including a shared key. So we can go on with the policy, for authentication I still use the default policy (all users), but for authorization we create a new one. In my test environment I putted all the users which may authenticate on the web to a group called GG_WEBAUTH, so it easy to define the matching criteria. By default there is no encryption, so we use PAP for authentication (don’t know yet, if you can change this). After creating the matching criteria, we have to set the vendor specific attributes, for Cisco this is the “Cisco-AV-Pair” attribute. I added 2 parameters to this attribute
priv-lvl=15 ip:inacl#100=permit ip any any
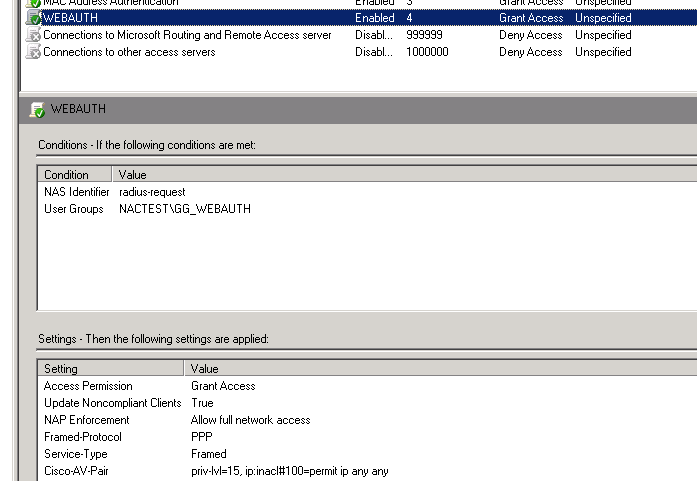
Of course you can change the number, you can even add more numbers to create longer ACL’s. With this two parameters your web-auth profile should work. There should also be a way with the ACL defined on the switch and make use of the filter-id attribute, but I was unable to get this to work.